Deep Dive - A Continuous Remediation Cycle
Overview
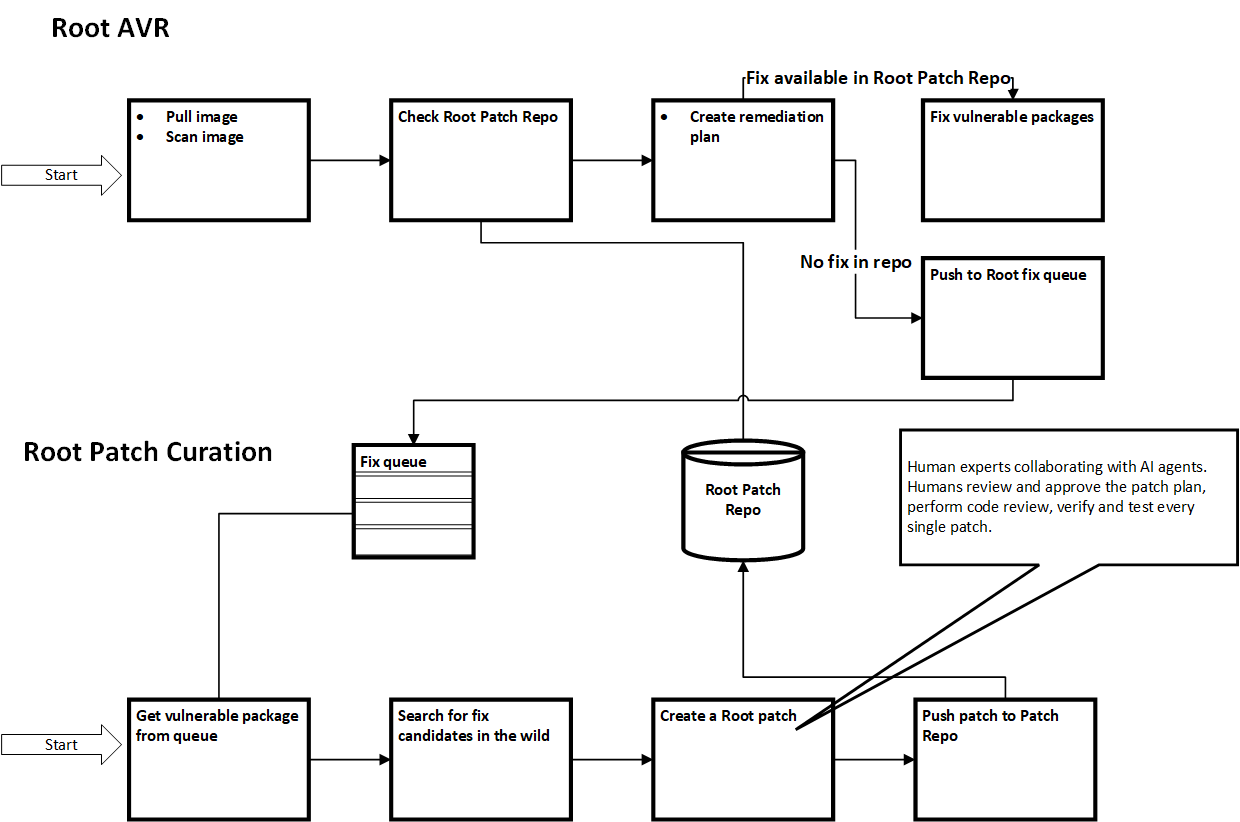
The Root platform operates as a continuous vulnerability management cycle, constantly monitoring for new security issues and remediating packages as soon as threats are identified. This ongoing process employs two main components that work in tandem: AVR and Root Patch Curation. Root's approach combines agentic AI with human expertise to ensure safe, production-ready results. A description of each process appears below followed by a high-level flow diagram that shows their interaction and the continuous nature of the vulnerability management cycle.
AVR - Remediation Process
AVR, Agentic Vulnerability Remediation, is an online process in which Root analyzes and remediates vulnerable packages in your container image. At the heart of this flow is the application of fix packages to replace vulnerable packages in the image. When compatible upstream packages from the distributor are unavailable Root curates a backported patch from an existing validated fix. For an in-depth explanation, see Root AVR Remediation Flow.
Root Patch Curation
Root Patch Curation is an offline process in which Root's agentic fleet operates in tandem with humans in the loop to gather healthy packages (no CVEs) that replace each vulnerable package in the queue. This human-AI collaboration is a critical differentiator, ensuring automation and expert oversight combine to deliver safe, production-ready results.
The process begins by checking for compatible native distribution package upgrades. If none is available, Root initiates the creation of a Root Patch, often involving backport patches to address specific vulnerabilities. Once curated, these Root Patches can be applied automatically to future images when the same vulnerability is detected, creating compounding value over time as Root's fix library grows.
High-Level Flow
The diagram below shows the full Root remediation cycle.
For further details, see:
Root - a continuous vulnerability management cycle
Updated 3 months ago