Quick Start
On this page we will give you a quick walkthrough of the Root workflow, from signing up and integrating your registry, through remediating images and reviewing vulnerability reduction. For each step you'll see links to further details.
For a Super Quick StartFor a super quick start, go to Step 1 - Sign Up, then jump to Step 3 - Remediate.
1️⃣Sign Up
To sign up for Root:
-
Go to Root.io and click Try Root.

-
Either click Continue with Google, or enter a username, email address and password, and then click Sign Up.
-
On the next page you will be prompted to enter the name of your organization and click Create your organization.
IMPORTANTChoose your organization name carefully—all users in your organization will share the same org name.
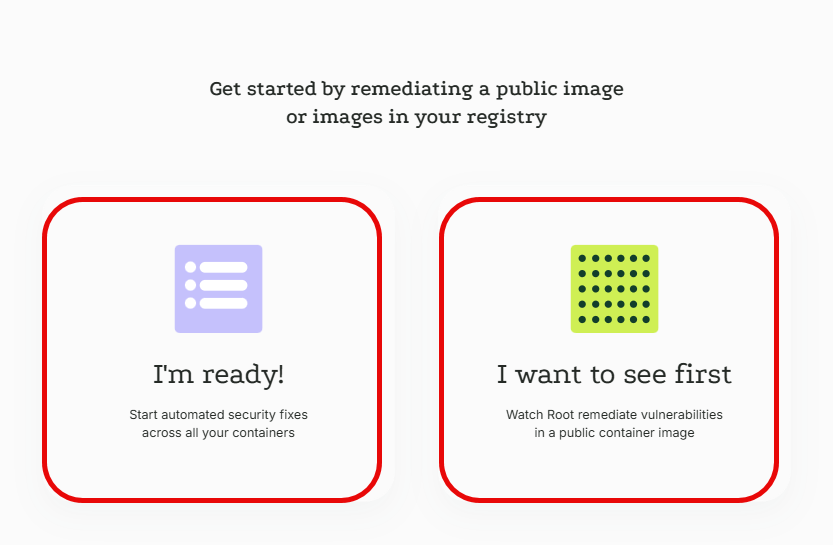
Now choose I'm ready if you want to go ahead, integrate your image registry with Root and start remediating your private container images, or I want to see first if you'd first like to give it a test run with a public container image.
2️⃣ Connect Your Private Image Registry
Now you can see how Root seamlessly and quickly scans and fixes your container images. Note that Root fixes your private images directly without rebuild or base image changes.
Note: If you'd like to see how it works before integrating your private image registry, skip to step 3, Remediate an Image, and choose the option for remediating a public image.
3️⃣ Remediate an Image
Run a Root AVR scan on an image and see how Root handles package vulnerabilities, enhances your security, and saves you time. During Remediation, Root applies version-safe security patches and Root patches directly to the container image in-place, returning a production-safe fixed image to your registry without requiring a rebuild or rebase.
- See Remediate Image.
4️⃣ Take a Deeper Dive
Below is a super high-level description of how Root works. After reading this, we are sure that you'll want to know more, so take a look at Deep Dive.
Root comprises two main processes:
- AVR - During the Agentic Vulnerability Remediation process, Root scans your image, applies patches from its repo, and rebuilds the image with near-zero vulnerabilities. Packages for which no patch was available go into the queue for the Root Patch Curation Process, and when they become available are added to the fix repo. New patches will be applied during the next image scan.
- Root Patch Curation - When no compatible native package is available, Root's Intelligence Agents search 24/7 for fix candidates for known CVEs from various sources, including upstream package versions. Once identified, Root Patches are created through a process that combines Agentic and Human-in-the-loop capabilities. All fix packages are stored in the Root Patch Repository.
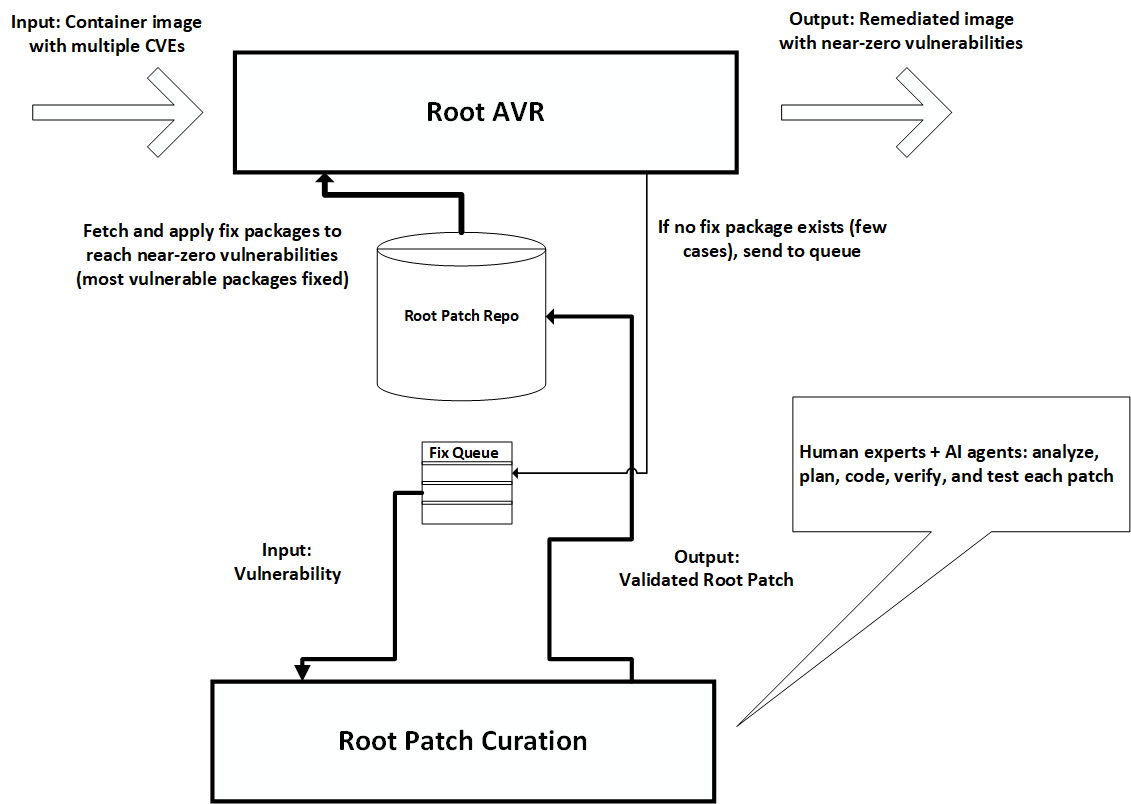
Root Online and Offline Processes - A Continuous Remediation Cycle
5️⃣ Review Scan Insights and Security Posture
Root's tools enable you to confirm vulnerability reduction, validate patch effectiveness, track overall CVE reduction achieved, and more.
6️⃣ Connect Root to Your CI/CD Pipeline
When you are ready to see the full power of Root, connect Root to your CI/CD pipeline and enjoy seamless image patching. This is as simple as adding another step in your build pipeline to call Root AVR. This way, Root can scan and remediate your images with no intervention on your part and you can view details whenever you want on the Root admin platform.
7️⃣ Invite Teammates
Invite teammates and assign them roles - Admin, Member, or Read Only.
Updated 3 months ago
Now explore the topics below to move ahead in your Root journey: