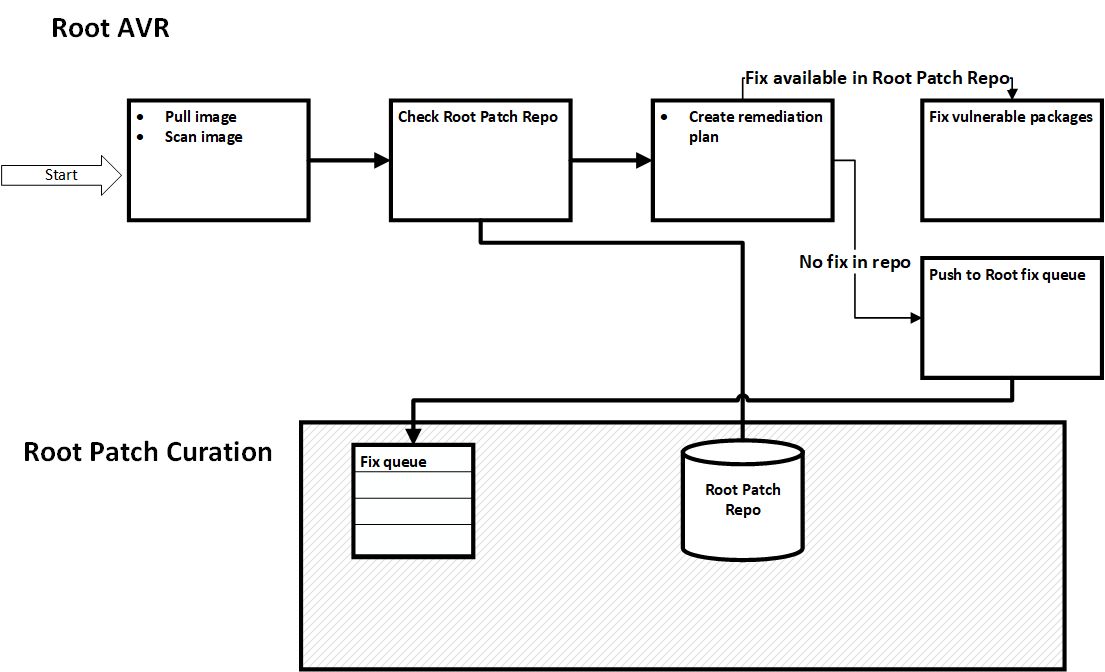
Root AVR Remediation Flow
Overview - Agentic Vulnerability Remediation - AVR
AVR, Agentic Vulnerability Remediation is the process we use to quickly and thoroughly scan your images, identify vulnerable packages (i.e., those with CVEs), swap out vulnerable packages with fix patches, and provide a remediated image with near-zero vulnerabilities. The AVR process is fully automated. It can be initiated from the Root admin portal, CLI, or via script and requires no monitoring or intervention. However, if you'd like to understand how things work behind-the-scenes, read on.
The main phases of the Root AVR process are described below.

1️⃣Pull
Root pulls the designated image (whether public or private) from the source registry into the AVR processing environment for scanning, evaluation, and preparation for remediation.
2️⃣Scan for Vulnerabilities
Root employs best-in-class Software Composition Analysis (SCA) scanners to scan your image for vulnerable open source components. Complete scan results are stored with comprehensive metadata for each affected package, including package name, ecosystem, distribution release, CVE identifier, and severity rating.
The diagram below illustrates the result of a SCA scan on a container image with a large number of vulnerable packages.
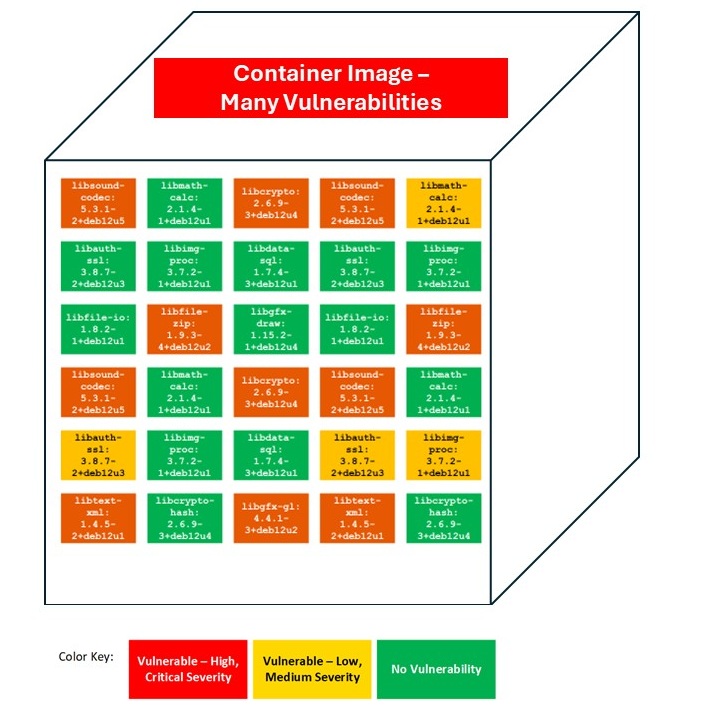
3️⃣ Evaluate
In this phase, Root determines if the image is eligible for remediation based on OS, architecture, and package ecosystem support. This evaluation occurs after vulnerability scanning. See Support Matrix
4️⃣ Remediate
Create Remediation Plan
After uploading the scan results, Root creates a remediation plan to fix vulnerable packages identified during the scan.
For each vulnerable package the remediation plan may indicate one of these:
- Native distribution package upgrade available
- Root Patch available
- Add to fix queue - If no fix is available, Root adds the vulnerable package to its work queue. Over the coming days, Root experts and AI agents will then curate a backported patch from an existing validated fix, or create a new patch from scratch, if none exist upstream. This entire process is monitored and validated by human experts. When available, these fixes will be applied during the next image scan.
Deeper DiveRoot AI agents, in collaboration with human security and coding specialists, work around-the-clock, researching, analyzing, and coding in order to create packages to stock the Root fix repo.
Implement Remediation Plan & Apply Fix Layer
Next, we implement the remediation plan by (1) updating the package manager configuration in your image to reference the Root image registry, and then (2) applying a new layer containing the native distribution package upgrades and Root patches directly to your existing image. This new layer preserves the original base image and application layers, applying all Root fixes in a single additional layer.
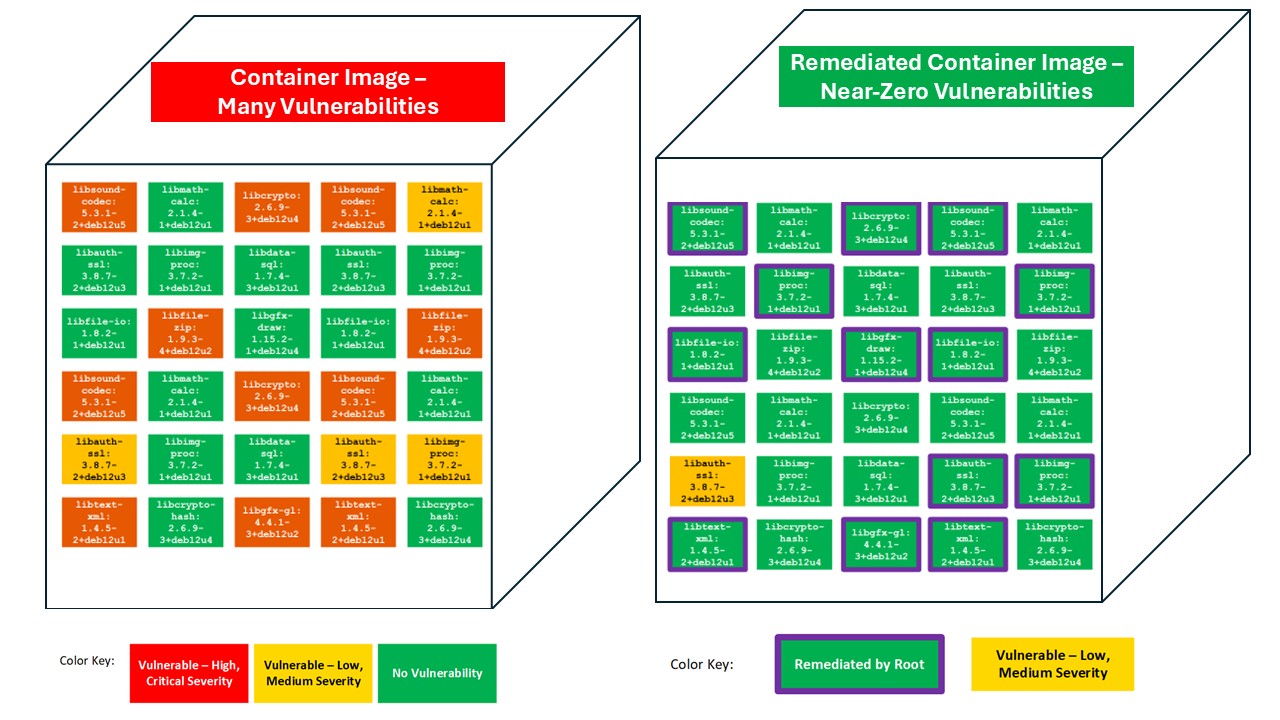
The example on the left below illustrates an image with multiple vulnerabilities. The image on the right illustrates the same image after Root Remediation. By applying Root Patches the container image has achieved near-zero vulnerabilities.
Note
See here for an explanation of how Root handles versioning and numbering of remediated images and patches.
5️⃣ Rescan
Once again, we scan the image to verify that fixes were applied correctly, that vulnerabilities are resolved, and that applied patches do not introduce regressions or break application functionality.
6️⃣ Push
Root pushes the remediated image back to your registry with updated SBOM and VEX artifacts that reflect the applied Root patches for traceability and compliance. Furthermore, the image metadata is stored in Root's registry.
When you remediate a public image, the remediated image is stored in Root's registry and available for download for 15 minutes.
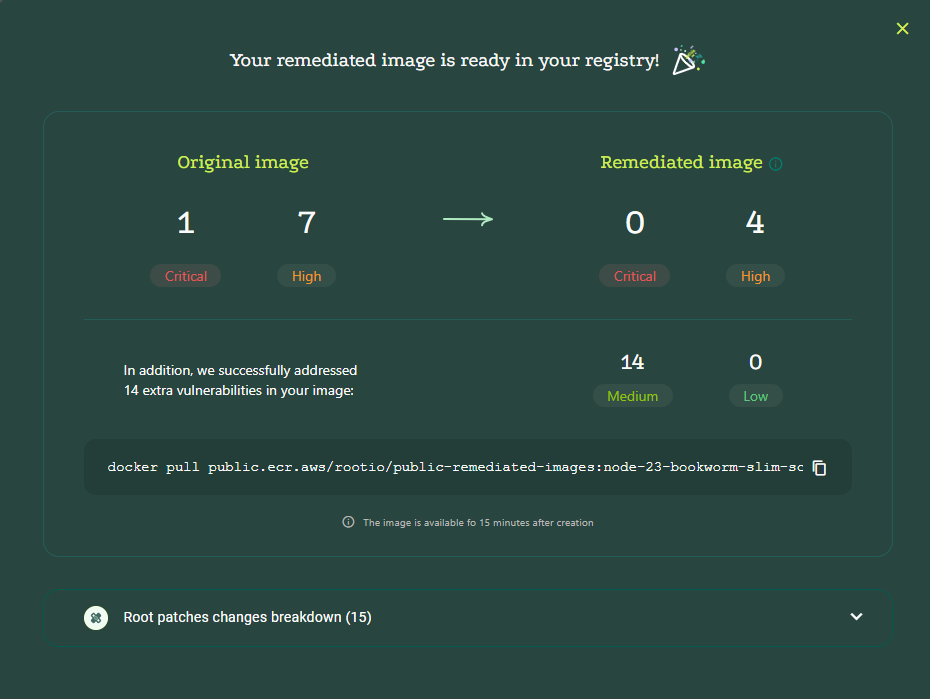
Summary - Remediation Complete
A summary of the remediation details is displayed. It shows the highest level details of the remediation such as the number of critical and high CVEs before and after remediation. From here, you can click on to see detailed results in Artifact Explorer - TBD.
Updated 3 months ago